At WakeUp Labs, we are submitting our technical proposal for the Cross-Chain Key Management for Safe Mission, aligned with Optimism’s Superchain interop goals.
Please verify that your team members below:
- Team Lead: WakeUp Labs
- Contact info: optimism@wakeuplabs.io | https://wakeuplabs.io | https://x.com/wakeuplabs
- L2 recipient address: oeth:0xAABA37Fb284667647D315B9D45C1830598B24081 (WakeUp Labs Safe on Optimism)
- Please list the members of your team and link to any previous work:
- WakeUp Labs is a Web3 infrastructure studio founded in Argentina in 2022, building open developer tooling and automation for DAOs, Corporations and protocols across Optimism, Arbitrum, Coinbase, Rootstock, Starknet, and others.
- Core team: Milton Berman (Co-Founder & CEO), Gonzalo Silman (Co-Founder & COO), Maximiliano del Hoyo (Co-Founder & CBDO).
- Contributors: Franco Perez (Engineering), Juan Dahl (ZK & Smart Contracts), Nahuel Jaume (SDKs & Integrations), Christian Escalante (Tech Lead), Matias Zapata (Software Engineer)
- GitHub organization: https://github.com/wakeuplabs-io
- Previous Optimism-related work includes:
- Superchain Accounts → GitHub - wakeuplabs-io/superchain-accounts
- RetroPGF Impact Evaluation Framework → https://github.com/wakeuplabs-io/retro-pgf-impact-framework
- zkID + OP Attestations → https://github.com/wakeuplabs-io/zkid-attestations
- Superchain Interop Alerts SDK → GitHub - wakeuplabs-io/op-interop-alerts
What makes your team best-suited to execute this Mission?
- WakeUp Labs is an established contributor within the Optimism ecosystem, having successfully completed previous Governance Fund Missions and RetroPGF-funded projects focused on interoperability, automation, and public goods.
- The team has deep experience developing Safe-based modules and interop infrastructure, including fully on-chain reward automation for Velora DAO using UMA’s oSnap module and cross-chain health monitoring for OP Stack environments.
- We combine technical expertise (smart contracts, SDKs, interop systems) with strong alignment to Optimism’s Impact = Profit values, ensuring the outcome will be open-source, reproducible, and beneficial to the entire Superchain.
Please describe your proposed solution based on the above:
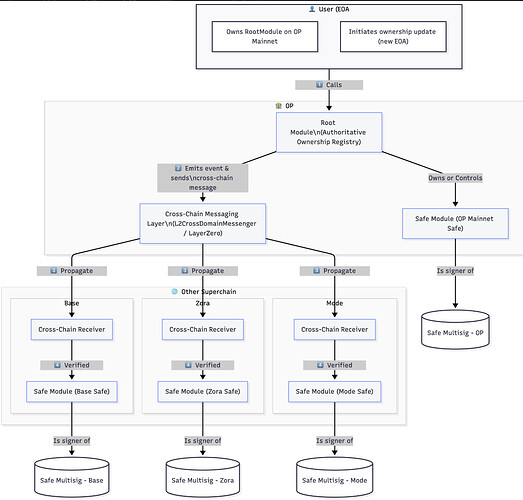
We propose building a Cross-Chain Key Management Module for Safe, designed to enable unified signer management across the Optimism Superchain (Optimism, Base, Mode, Zora, and other OP Stack chains).
Goal
When a Safe owner rotates a signer (for example, replacing an EOA), the change will automatically propagate across all connected Safes, eliminating manual per-chain updates, preventing inconsistent signer states, and improving both usability and security.
High-Level Architecture
Components and Roles
| Component | Role |
|---|---|
| RootModule (Hub) | Deployed on a canonical chain (e.g., OP Mainnet). Acts as the authoritative registry of current Safe signers and initiates updates. |
| ChildModule (Spoke) | Deployed on each Superchain chain. Receives and applies signer updates from the RootModule via Safe’s execTransactionFromModule. |
| Cross-Chain Messenger | Handles secure message delivery between RootModule and ChildModules. Initially uses Optimism’s L2CrossDomainMessenger, later adaptable to the upcoming OP Interop protocol or external messaging layers like LayerZero. |
| Safe Multisig | Integrates the ChildModule as a trusted module. Signer updates are executed through Safe’s standard module interface. |
Update Flow
- The Safe owner or Root Safe calls one of the module’s functions:
addSigner(address signer)– add new signer
revokeSigner(address signer)– remove signer
rotateSigner(address oldSigner, address newSigner)– replace signer - The RootModule serializes and dispatches the update to all registered ChildModules through the cross-chain messenger.
- Each ChildModule verifies message authenticity and executes the corresponding Safe transaction:
addOwner(signer)removeOwner(signer)swapOwner(oldSigner, newSigner)
- Each Safe updates its local signer list, maintaining consistency with the RootModule state across the entire Superchain.
- Protection mechanisms include:
- Nonce tracking to prevent replay attacks.
- Verification that all messages originate from the legitimate RootModule.
- Optional recovery function
syncFromRoot()to handle delayed or failed messages.
Please outline your step-by-step plan to execute this Mission, including expected deadlines to complete each piece of work:
Total Estimated Duration: 9 weeks
Milestone 1 – Research & Planning (2 weeks)
Objectives
- Finalize architecture and module specification for cross-chain signer management.
- Produce design diagrams, security model, and Root ↔ Child state-sync logic.
- Validate cross-chain communication feasibility between OP Mainnet and one Superchain chain.
Deliverables
- Architecture and specification document.
- PoC demonstrating Safe transaction execution without manual signer approval.
- PoC for message send/receive between OP Mainnet and another OP chain (e.g., Base or Mode).
Acceptance Criteria
- Successful cross-chain message transmission and log verification between two Superchain testnets.
- Completed technical report covering Root, Child, and Messenger components.
Milestone 2 – Core Development (3 weeks)
Objectives
- Implement RootModule and supporting contracts.
- Enable full signer rotation propagation across multiple chains.
- Develop unit tests and deployment scripts.
Deliverables
- Solidity contracts for RootModule and ChildModule.
- Cross-chain propagation functional on more than two Superchain testnets.
- Registration scripts for Safe integration.
Acceptance Criteria
- Ownership rotation executed on RootModule propagates to five chains in under five minutes.
- All core logic and event flows covered by automated tests.
- Live demo.
Milestone 3 – QA & Reliability (3 weeks)
Objectives
- Reinforce reliability and state synchronization across networks.
- Implement recovery and re-sync for failed or delayed message deliveries.
- Develop monitoring and validation tools for signer consistency.
Deliverables
- Recovery function
syncFromRoot()for manual state repair. - QA report verifying propagation and synchronization integrity.
Acceptance Criteria
- Demonstrated recovery of a failed rotation via
syncFromRoot(). - Consistency validated across all tested chains.
Milestone 4 – Audit & Finalization (1 week)
Objectives
- Apply to Optimism’s subsidized audit program.
- Address and document any feedback received.
- Prepare audit-ready documentation.
Deliverables
- Updated and audited contracts.
- Final documentation, SDK integration guide, and public report.
Acceptance Criteria
- Audit request submitted and feedback incorporated.
- Finalized public release repository (open-source under MIT license).
Please define the critical milestone(s) that should be used to determine whether you’ve executed on this proposal:
- Milestone 1: Successful cross-chain message delivery between OP Mainnet and one Superchain chain (Base or Mode).
- Milestone 2: RootModule signer rotation propagates to five chains in under five minutes with full test coverage.
- Milestone 3: Verified recovery and synchronization mechanism operational.
- Milestone 4: Audit request submitted and all feedback implemented.
Please list any additional support your team would require to execute this mission:
- Access to OP Labs documentation and engineering guidance regarding OP Interop protocol (when available).
- Subsidized audit through the Optimism audit grant program.
- Optional technical alignment review with Safe Global’s engineering team.
Acknowledgements
![]() I understand my grant for completing this Governance Fund Mission will be locked for one year from the date funds are transferred to the locked multisig wallet.
I understand my grant for completing this Governance Fund Mission will be locked for one year from the date funds are transferred to the locked multisig wallet.
![]() I understand that I will be required to provide additional KYC information to the Optimism Foundation to receive this grant.
I understand that I will be required to provide additional KYC information to the Optimism Foundation to receive this grant.
![]() I understand my locked grant may be clawed back for failure to execute on critical milestones, as outlined in the Collective Grant Policies → Collective Grant Policies
I understand my locked grant may be clawed back for failure to execute on critical milestones, as outlined in the Collective Grant Policies → Collective Grant Policies
![]() I confirm that I have read and understand the Collective Grant Policies → Collective Grant Policies
I confirm that I have read and understand the Collective Grant Policies → Collective Grant Policies
Submitted on behalf of WakeUp Labs (contact: optimism@wakeuplabs.io)