Season 8 Intent: A set of interoperable Stage 1 chains doing $100m per month in cross-chain asset transfer
Total grant amount: Up to 126,000 OP (funding 63,000 OP per team, up to 2 teams)
Should this Governance Fund Mission be fulfilled by one or multiple teams: Up to 2
OP Labs or Optimism Unlimited Sponsor: Pierce
Reviewing Body: Developer Advisory Board Foundation Mission Team
Submit by: October 31, 2025
Selection by: November 7, 2025
Start date: November 14, 2025
Governance Fund Mission Request
Cross-Chain Key Management for Safe
Consider this scenario:
- An EOA is a signer on a Safe multisig deployed across multiple chains.
- To update the signer to another address, signers have to propose, verify and sign tx on all these chains.
This ops heavy task leads to increased costs, time delays, and potential security risks from inconsistent states.
We invite proposals for building a Safe module which enables unified key management across the Superchain ecosystem.
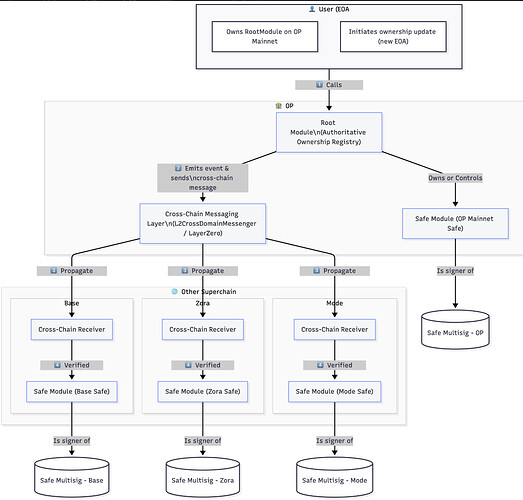
Here is a high-level architecture of this Safe module based system:
This module can be assigned as a signer for Safe multisigs deployed across Superchain. This module, in turn, is owned by the address of the end user (an EOA for example).
To replace its address with another, the user updates the owner of the Safe module, which then communicates this change to modules deployed on other chains in Superchain. These modules then update their owner, effectively updating the signer on all the multisigs, thus removing the need for action from the user.
Proposing teams are free to choose other architectures if they can demonstrate clear advantages.
How will this Mission help accomplish this Season’s Intent?
Cross-chain key management remains a challenge. As the Superchain ecosystem grows, cross-chain key management becomes more and more complex as the user has to take action on multiple chains.
With Safe being the popular choice for multisig contracts, reducing the maintenance cost to operate them should positively impact cross-chain asset transfers as users are more likely to deploy Safe multisigs on different chains.
This system can be updated to use interop when it ships.
What is required to execute this Mission?
Technical Requirements:
- Development of a Safe module smart contract that can be deployed across all Superchain networks
- Implementation of cross-chain messaging infrastructure
- Creation of a root/hub module that manages ownership state and propagates changes to child modules
Deliverables:
- Open-source smart contracts with comprehensive documentation
- Tests and deployment scripts
- Integration guide for existing Safe deployments
How should progress towards completion be measured?
- Milestone 1:
- Completion of module architecture design and specification
- Successful deployment of prototype on testnet across at least 3 Superchain chains
- Milestone 2:
- Successful ownership update propagation across 5 Superchain chains within 5 minutes
- Milestone 3:
- Apply for audit grant. If audit received, address audit feedback.
Application Instructions
To apply for this Governance Fund Mission, please complete the form in the expandable section below and leave your response as a comment on this forum thread. Submissions will be open until Oct. 10th, at which time the Developer Advisory Board will review all submissions and select up to 2 individuals/teams to complete the work defined here.
Submission Form
Submission Form
Copy the entire application below and leave a comment on this issue with your answers completed. A representative from the Developer Advisory Board may reach out using the contact info provided to request more information as necessary.
Governance Fund Mission Application
Please verify that your team members below:
- Team Lead: Please specify the best point of contact for your team
- Contact info:
- L2 recipient address:
- Please list the members of your team and link to any previous work:
What makes your team best-suited to execute this Mission?
- […]
- […]
Please describe your proposed solution based on the above:
- […]
- […]
Please outline your step-by-step plan to execute this Mission, including expected deadlines to complete each piece of work:
- […]
- […]
Please define the critical milestone(s) that should be used to determine whether you’ve executed on this proposal:
- […]
- […]
Please list any additional support your team would require to execute this mission:
- […]
- […]
Please check the following to make sure you understand the terms of the Optimism Foundation Mission program:
- I understand my grant for completing this Governance Fund Mission will be locked for one year from the date funds are transferred to the locked multisig wallet.
- I understand that I will be required to provide additional KYC information to the Optimism Foundation to receive this grant
- I understand my locked grant may be clawed back for failure to execute on critical milestones, as outlined in the Collective Grant Policies
- I confirm that I have read and understand the Collective Grant Policies